Part One:
In Part One of this series, we will cover the basic fundamental knowledge of Ethereum, what is it, how does it work, what are the primitives of Ethereum and its structure.
What is Ethereum 🌎
Ethereum is an open source distributed ledger that was originally proposed in late 2013 and then released to the public in 2015 by a Canadian called Vitalik Buterin. He was originally born in Russia and then he migrated as a child to North America. With an IQ of 150+ and a strong technical mind, he came up with the idea for Ethereum after analysing the bitcoin blockchain and queried if things could be taken further by making a blockchain that is Turing complete, and therefore be able to read scripts of code and run applications in a trustless manner.
Turing complete — Means that the computer or machine can solve a mathematical equation given the correct algorithm along with the necessary time and memory.
How does Ethereum work ? ⚙️
Ethereum works as a p2p decentralised protocol whereby all participants in the network will connect to each other through the Internet to share and retrieve the state of the blockchain.
Ethereum is built upon a virtual machine called the EVM (Ethereum Virtual Machine) which allows smart contracts to be compiled down into EVM compatible bytecode and deployed to the blockchain for execution. While the EVM itself is a 256 bit register stack which is designed to run the same code exactly as intended time after time.
Once a piece of code is deployed to the Ethereum blockchain, it lives there forever in bytecode and can be accessed through a unique contract address which is given to each and every contract deployed to the blockchain. When you send a transaction to the contract address it will get propagated to the network of miners, whom then have to race to perform a mathematical equation where the outcome is within a certain range. This is called a consensus mechanism which is commonly known as Proof-of-work (PoW) once a miner hits the number in required range they can then add their block to the chain to finalise all the transactions within that block. The same actions are carried out for all transaction that happen on the Ethereum blockchain unless they are reverted due to gas fees or a requirement error.
nodes/miners 💻 ⛏
Nodes and miners are very similar in the way they operate apart from one factor mining. Mining nodes will compete against each other in a race to find a number which gives them the right to add a new block to the chain. In Ethereum there are 3 kinds of nodes you can sync with either the Go-Ethereum software (geth) or the Parity software, the go-ethereum node is the most commonly used in the Ethereum eco-system, while Parity is still a big part of Ethereum the community is very much geared towards developing with Go-Ethereum.
All kinds of nodes are considered participants in the network and will hold either a full copy of the blockchain from the genesis block (The first block in the chain) or a lite version of the blockchain whereby the state of the node will only hold the current state of the blockchain and retrieve the necessary data from the merkle trees of full archive nodes when in sync mode.
To set up a node on your machine please download the binary folders for Go-Ethereum (https://geth.ethereum.org/install/). Once downloaded you can start to use the following commands in your terminal or powershell to begin an instance of the blockchain:
geth console - for a full node. ChainId - 1
geth --light console - for a light node. ChainId - 1
Networks 🛰
There are also different networks in Ethereum, such as Ropsten, Rinkeby and Kovan. The Ropsten, Rinkeby and Kovan networks are test networks for trials and development of the blockchain. The Ropsten network operates on the same consensus mechanism as the main chain (Proof-of-work) but the other two are Proof-of-Authority networks, which means only certain nodes can mine blocks that get put onto the chain. To set up a Ropsten, Rinkeby or Kovan node you would use the same command as the main net although this time you would need to switch the network name with the word “console”.
Use the following commands to start a test network node:
geth --testnet - for the ropsten network. ChainId - 3
geth --rinkeby - for the rinkeby network. ChainId - 4
geth --dev console - for a local developer console. ChainId - NONE
To access the kovan network you must first download Parity and then use:
parity --chain=kovan - for the kovan network. ChainId - 42
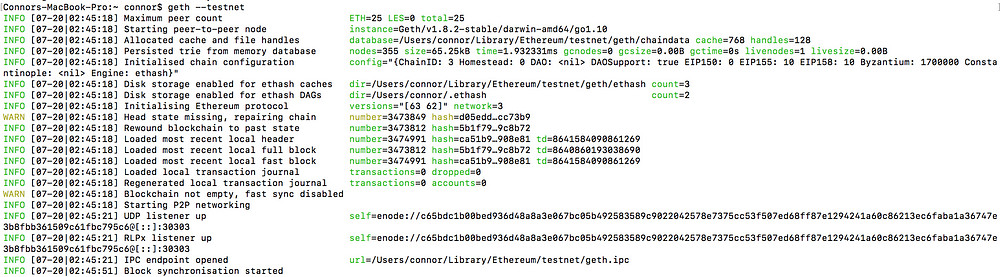
Go-Ethereum node
Primitives of Ethereum ♦️
Ethereum holds most of the same common primitives of all the public blockchains such as public key cryptography, cryptographic hash functions, merkle trees and forks. Now you may think these concepts sound a little technical or scary but please don’t fear for the Wiseman is here, to guide you through and once you understand the following you shall be well on your way to becoming a blockchain wizard! Because nearly all of the public blockchains will be using these primitives. So things from here on out should not be too cumbersome to understand when conducting research or just having a little read up on the latest decentralised protocol.
Public key cryptography 🔑
Public key cryptography also known as asymmetric cryptography, provides users with a key pair that is one public key and one private key, these keys are derived from the elliptical curve ecp256k1 algorithm which is used for all of the Ethereum addresses that operate on all the networks. These key pairs provide the user with two features:
Encryption: Whereby only the private key can decrypt a message that was encrypted with the corresponding public key.
Authentication: So that a public key can verify ownership of a private key in the form of a digital signature.
The public and private keys come in hexadecimal form and will look like
public key - 0x84c3492F47bF06C0F994E468C364CF52b3676d0d
private key - 83d01607d74d9b100d356d68ea2c7ac795aca429bf20f305f63d484313a1e60b
Cryptographic hash functions 🔐
A cryptographic hash function is a hash functions which takes an input or ‘message’ and returns a fixed size alphanumeric string. The string is called the hash value, message digest, digital fingerprint, digest or checksum.
A hash function has 3 main properties.
1: It is extremely easy to calculate a hash of any given data. (Easy to calculate forwards)
2: It is extremely computationally difficult to calculate an alphanumeric text that from a given hash. (Near impossible to calculate backwards)
3: It is extremely unlikely that two slightly different messages will have the same hash. (Collision resistant)
Why use hash functions ? 💡
Ethereum uses hash functions to provide anonymity to the users of the blockchain and also give them a certain level of privacy so the whole world does not know there business. Hash functions give the blockchain the power to hide messages, identity and various other forms of important information, which people may not want public, hash functions also provide a way of certifying the integrity of the data that is on the blockchain. How this happens is through digital signatures whereby the cryptographic key pair will sign the message or data being added to the blockchain. And then the hash function will spit out a hash that has the message or data and the public key from the cryptographic key pair encrypted into the digest to be added to the blockchain. Then when data or message is needed to be revealed the owner of the public/private key can decrypt the digest with their private key to give a proof of truth or ownership to the entity or person in which the digest is being revealed to.
Merkle trees 🌳
Merkle trees in computer science and cryptography are used to store, handle and transfer data between computers on a p2p network. They help ensure that the data received from other peers in a p2p network is undamaged and unaltered, they can also check to make sure other peers in the network are not behaving maliciously and sending or creating fake data on the blockchain. They work by having every leaf node labelled with the hash of a data block, while every non-leaf node is labelled with the cryptographic hash if the labels of its child nodes. Hash trees allow for efficient and secure verification of the contents of large data structures, which is useful for Ethereum because the sheer amount of data that gets added to the blockchain does have the potential to be manipulated by a hacker. But in the case of a merkle tree if one hash changes then all of the hashes change, and the network will know that the security of the blockchain has been compromised.
Blockchain forks 🍴
When talking about blockchains there are two types of forks, hard forks and soft forks. When ever a fork happens it means that the chain-data has been compromised through an act of manipulation on the network, a hack where as funds have been lost or stolen, when two parties of network nodes decide on different way the chain should operate or when two blocks are found by the network at the same time but propagated across a different subset of nodes.
A worst case scenario for Ethereum or atleast the one the community wishes to avoid as much as they can is a hard fork, this is because when a hard fork happens a whole new chain is started and leaves the old chain behind. When this happens the integrity of the blockchain is compromised and all the data from the chain that people are leaving behind is now in-accessible on the newly forked chain. You may have heard about the DAO hack which resulted in $70,000,000 worth of ether being stolen from the contract, this was because of a recursive call vulnerability which the developers did not see and the then hacker exploited.
http://hackingdistributed.com/2016/06/18/analysis-of-the-dao-exploit/
The DAO hack was resolved by a hard fork and the stolen ETH would be paid back to the investors from whom it was stolen. A few high profile members of the community helped in hacking back some of the stolen ETH from the hackers account to bring back to the community.
A soft fork on the other hand only happens when a new piece code is being added to the protocol or more commonly when, two nodes are mining on opposite sides of the globe, they both create a new block and hit the required ranged number to add the block to the chain. The new block will then be propagated across the network and added to the chain by all the connecting peers one after another until. You hit a point where you have a node trying to add two blocks with the same number from different miners, what happens is the the blocks both get added to the chain but only the block that was distributed across more of the network than the other will have the next block added on top.
Now you may be thinking what there are two blocks but only one block continues to get mined on but what happens to the other block ?
The other block will continue to get mined on as-well but only until the mining nodes of the network realise that there is a fork in the chain and that they must stop mining on the smallest chain. The miners will realise this by the hashing power they are using compared to the rest of the network.
Also they will be breaking one of the 3 rules of mining a blockchain which are
1: Miners must always mine on the chain they are given first.
2: Miners must always mine on the longest chain.
3: Miners must always hit a number within a certain range before adding the next block to the chain.
The structure of Ethereum. 🏛
Ethereum as an organisation or foundation holds a flat hierarchy with the main point of direction coming from the creator Vitalik Buterin. The main aim of governance in Ethereum is to operate as a decentralised autonomous organisation or DAO, that allows anyone to put forth proposals (EIP’s/Ethereum Improvement Proposal) contribute to the code base and help with community projects such as Casper the friendly ghost also known as the Ethereum Proof-of-Stake(PoS) consensus mechanism, Plasma, Sharding, State channels, Token-economics, zk-starks & snarks and many more.
Ethereum also has created the EEA (Ethereum Enterprise Alliance) which is a nonprofit organisation that has over 150 members and partnerships which include blockchain start-ups, fortune 500 companies and researchers such as Toyota research institute, J.P Morgan chase, Samsung SDS, ING, Microsoft, Intel, Consensys and Mastercard. Some of these companies may be as corporate as they come but with big players and influential partners the EEA will be able to succeed in bringing the world the decentralised web3.0. Along with countless new opportunities for innovation in places and peoples lives that were never possible before Ethereum.
This kind of structure will also bring a new way for the world to interact with its leaders and monopolies, through a concept of on chain governance and voting, whereby the demographics of the Ethereum foundation, the EEA and the planet as a whole will not be as it is today, but it will be a place where the people of the world will be able to use the blockchain to vote on matters or problems they feel need to be fixed with a swift and diligent manner.
Credits: Connor Wiseman