Trust
“There is one thing that is common to every individual, relationship, team, family, organization, nation, economy and civilization throughout the world — one thing which, if removed, will destroy the most powerful government, the most successful business, the most thriving economy, the most influential leadership, the greatest friendship, the strongest character, the deepest love. On the other hand, if developed and leveraged, that one thing has the potential to create unparalleled success and prosperity in every dimension of life. That one thing is trust.”
The speed of Trust, by Stephen M. R. Covey with Rebecca Merrill
Trust is a sine qua non of Digital Economy, and honesty is not ethical, but an economic issue says Don Tapscott and Alex Tascott (2018). Trust means depending on people, institutions, intermediaries or even things for mundane to essential matters of life. With trust, humanity has built centralised trust-based and powerful systems such as governments, financial, health institutes and other intermediaries leading us to our modern civilisation. However, as Don Tapscott and Alex Tascott (2018) mention, trust implies vulnerability and the people, governments, and companies we trust may fall short of honesty, consideration, accountability and transparency and loose trust amongst each other. When that happens, the trust-based system falls apart in implications on the loss of time, money, energy and reputation. Many activities require trust.
According to a Trust expert, Rachel Botsman (2017), “we are at the tipping point of one of the biggest social transformations in human history with fundamental consequences for everyone and new world order is emerging”. She points out that while there may be loss of faith in institutions and leaders, millions of people are placing their trust to rent homes, buy taxi rides and exchanging digital currencies, goods and services amongst total strangers.
Without trust in the government, a currency note is valueless, without election commissions, a vote in an election is only a pointless ritual, and without a trusted peer-to-peer taxi ride service company someone offering a ride in their car could be a potentially dangerous stranger. However, since the last ten years, the Bitcoin and similar inventions have shown us that currency or transfer of value can be trusted without trusting anyone in particular to verify transactions. Bitcoin focused on the decentralization of trust with value exchange without the need for trust or central authority.
Using DLT/Blockchains records/blocks can be updated with non-erasable information via a predefined consensus protocol. Consequently, creating verifiable and visible footprints to serve as a trust-machine, that allows establishing facts, fending off the dependencies for intermediaries and dissipating the murky clouds of alternative truths and fake information. Propelled by the game-changing, disruptive and innovative, DLTs and Blockchains technologies, we probably are at the advent of the age of distributed trust, a paradigm shift enabling transparency in decisions, actions and transactions, bringing back consumer control
Information Security
Blockchains are guarded by highly sophisticated encryption techniques for disguising and revealing information and to protect records, ledger, and transactions from any tampering. This is commonly done through a method known as the Asymmetric Cryptography (Public Key Cryptography) that uses a public key to encrypt a message and a private key to decrypt it.
A private key serves as input for the algorithm to produce its corresponding public key, but the same public key cannot be reverse-engineered to produce its corresponding private key, due to the one-sided nature of this algorithm. Each party generates its own public-private key pair. Private keys are meant to be kept secret and a public key could be freely distributed between parties. A sender can use the public key of the intended recipient to encrypt information and the recipient can decrypt the same using recipient’s private key. Any message encrypted with a private key can only be decrypted with the corresponding public key. If a private key is lost, everything that is controlled by the key is lost as well. There is no third party on the Blockchain to call for help in this case!
There are different types of Asymmetric Cryptography methods such as RSA (Rivest-Shamir-Adleman), and ECC (Elliptic Curve Cryptography) used for Blockchains. For example, in case of Bitcoin, private keys are used to produce a public key using Elliptical Curve Digital Signature Algorithm (ECDSA), Zcash uses Zero-knowledge proofs (zk-SNARKs) and Monero uses Ring Signatures.
Also, once you send the cryptocurrency to a recipient, they can only receive it and deposit it into their account with the use of their own corresponding key. The same techniques also serve for entity authentication to verify identity and data origin i.e. it that the message sent from a given entity was actually sent by the same entity.
Security against data tampering also comes from the hashing of transactions data as explained above. Storing of the online ledger of all transactions on multiple nodes provides additional security against forgery, data loss and hacking.
Data Privacy
The Merriam-Webster defines privacy as freedom from unauthorised intrusion. Data privacy is not necessarily about secrecy or having something to hide. It is about control related to the use and disclosure of data (Cavoukian, 2017); the capability to choose whether the information is disclosed to others and determine how it is used, as mentioned by Steven T. Snyder (2019). Snyder also added that “The highest degree of privacy for an element of information would be if its owner had complete control over its dissemination and use for as long as the information exists” Also, that the enforcement of privacy is how security will be defined encompassing the mechanisms used to ensure the confidentiality, integrity and availability of information. The notion of control and freedom of choice is critical to privacy. According to Cavoukian (2017), respect for the privacy of all individuals in a society not only forms the bedrock of freedom but also of innovation and its resulting prosperity. However, data privacy is being eroded.
Large organizations see enormous potential and value in correlating vast amounts of data to decipher trends, interpret behaviour and formulate predictions. Data collected is intended for value-added services, such as to personalise and enhance the user experience, to offer suitable or new services, bring efficiencies and convenience to the end-user. This creates economic and social value, beneficial for business and considered as a highly valuable asset. Entities holding such data believe that this data is collected via various data collection techniques, investment, and obtaining consent. Therefore, it belongs to the data collector, and they should be the ones controlling it.
Consent is usually obtained through fine-print terms and conditions agreements. It is general knowledge that “no one reads that”. Mainly, because people have given up on making that effort, let alone being able to understand, against the convenience of ignoring and moving forward to get to what they want to do by using any particular service or application on the web. Most of us do not resent that our smartphones or wearable devices allow our location, activity or health status being tracked continuously for the ability to navigate our way or show our health or activity levels through a few clicks on an app. The biggest IT companies have gained enormous wealth by harvesting and commoditising the information by exploiting data about their users, who expect privacy.
With pendular inclinations towards their duties of citizen’s protection and privacy rights, governments collect data and perform uninvited or secretive surveillance for control, for protecting its citizens from harm, mostly justified in the name of security, detecting threats to the security or finding terrorists (“needles in haystacks”).
In both cases, what is stored where, how secure is it, whom it is shared with, how it is interpreted and what that leads to, is unknown? Not having answers to these questions contributes to the lack of transparency and erosion of our privacy, and as a result, loss of trust in third parties, that we depend on to run our modern lives.
According to United Nations Conference on Trade and Development (UNCTAD, n.d.), “107 countries (of which 66 were developing or transition economies) have put in place legislation to secure the protection of data and privacy. In this area, Asia and Africa show a similar level of adoption, with less than 40 per cent of countries having a law in place”. However, in the age of our fast evolution of the ubiquitous information technology, the law is, by and large, trailing behind the innovations. There is a growing gap between data privacy laws and the way information is collected, processed, stored, shared or ensured that it can be trusted to be consistent with the interests of the people; giving people control and freedom of choice.
DLT or Blockchain technology comes with a promise where:
- Users are not required to trust any third-party and are always aware of the data that is being collected about them and how it is used.
- The users are the owners of their personal data.
- Third parties can utilise the user’s data, as authorised, without being responsible for securing data. On a public Blockchain, details of every transaction can be made available, easily accessible by government agencies, business partners or even co-workers without the need for revealing their personal details, unless authorised
In case of cryptocurrency such as the Bitcoin, there is no room for a centralised or third-party intervention. Other than the transaction fee, all other details are concealed with no intervention between transaction parties. Although a log of every transaction is kept, personal information is protected by anonymising the data by only storing a hash value of people’s identity for the transactions. Therefore, information on a Blockchain cannot be used to trace transactions back to a particular individual just by examining a Blockchain, as it is nearly impossible to associate transactions with a real person’s identity.
Tracking, Transparency, Provenance and Immutability
Ability to track, with transparency, determining provenance and immutability are often essential drivers for Blockchain adoption for a given use case. Using supply chains as an example, it is easy to understand that multiple entities need to write and read information. Blockchain can serve as a common and shared ledger with immutable information to determine the ownership of an asset or the completion of a transaction. This can empower participants by providing them with an indisputable mechanism to verify that the data of a transaction has existed at a specific time including information on the origins of each asset or record and how its ownership has changed over (Alexandre Grech and Anthony F. Camillieri, 2017).
A record on a Blockchain remains immutable or unchangeable after it is created. To create and record a transaction, participants or nodes running the Blockchain protocol must come to a consensus on the transaction’s validity. After the valid transaction is recorded to the ledger, no participant can tamper with a transaction. Immutability of information serves as resilience and irreversibility, which provides security and integrity of data. Since, Blockchain data is replicated across many different locations or nodes, attempts to change data in one location or node raise suspicion, interpreted as fraudulent activity and an attack on the Blockchain integrity by other participants. There are scenarios such as a 51% attack (Frankenfield, 2019), where the change is forced through gaining control of the majority of nodes. It is very difficult and costly to achieve, especially on large network public Blockchain and there are countermeasures for that too.
Peer-to-Peer network, Decentralization and Disintermediation
Vitalik Buterin, the co-founder of the Ethereum Blockchain (Wikipedia, 2019), mentions Goodey (2018) that the “Blockchain solves the problem of manipulation. When I speak about it in the West, people say they trust Google, Facebook, or their banks. But the rest of the world doesn’t trust organizations and corporations that much. Blockchain’s opportunities are the highest in the countries that haven’t reached that level yet.”
In an interesting article, the author Scott (2018) explains “How the data ecosystem is becoming medieval and our modern digital ecosystem is rapidly organizing as a feudal power structure erected in parallel with our existing power structures and freedoms”.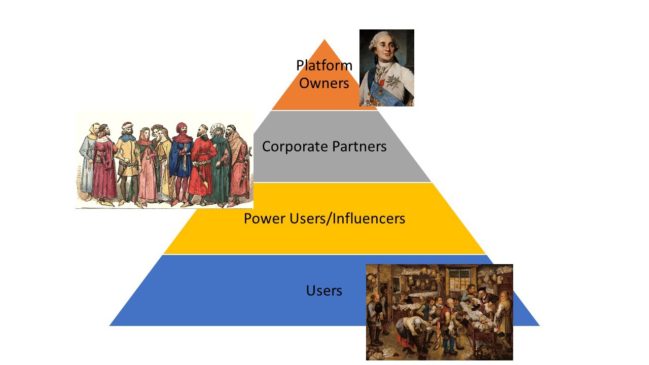
Figure – Classes of Digital Feudalism. Source: https://towardsdatascience.com
According to Scott, (2018), as shown in Figure 8, the “Lords and Kings” own and control massive digital platforms, “The Gentry” is Corporate Partners and Power Users who gain from their own sub-platforms, networks of sites built around their core audience, or lucrative full-time jobs distributed as rewards from platform lords and all the way below are the user, “The Serfs”are users who produce and surrender data in the course of their day-to-day lives. The lords of this “Digital Feudalism” system are tech company executives, whose entire infrastructure is built upon the collection and exploitation of user data.
We should not be able to trade what is not ours or what we are not authorised to trade (Don Tapscott and Alex Tascott, 2018). On a Blockchain, one owns one’s data. Blockchain has the potential to level the playing field by reducing the need for intermediaries or third party between two transacting parties, forming a peer-to-peer network, and that can be useful for many use cases. For example, as pointed by Alexandre et al. (2017), participants linked together in a marketplace through a common platform using Blockchains can conduct transactions and transfer ownership of valued assets with each other in a transparent manner and without the assistance or intervention of third-party mediators or intermediaries.
Idea is that such peer-to-peer interactions, with trusted code and algorithms, can potentially reduce or eliminate cost, friction, delays, and complexity related to third-party involvement. Alexandre et al. (2017), indicated that “Blockchains can reduce overhead costs when parties trade assets directly with each other, or quickly prove ownership or authorship of information — a task that, is otherwise currently next to impossible without either a central authority or impartial mediator”. Moreover, Blockchains’ ability to guarantee the authenticity of data and peer-to-peer, cross-institutional and cross-border boundaries can open possibilities of new ways of doing business and with whom it was not easy or possible before. For example, a farmer from remote developing regions could transact peer-to-peer with a retail shop in a developing world market. Payment to the farmer could be swiftly made directly without, heavy costs banking and commission cost and delays.
Ideally, a Blockchain is run by multiple nodes sometimes they may be in hundreds or even thousands. The nodes store multiple copies of the ledger i.e. the chain of records that contains copies of data or transactions. Data that is written on these transactions through a predefined method of verifying and validation. Therefore, decentralisation is at the core of Blockchain philosophy. It is a means to eliminate the need to depend on third parties and to protect the Blockchain against the intervention, control, manipulation or even shut down by third parties. For example, Blockchain-based cryptocurrency like Bitcoin is not controlled by any government or any other third party. Decentralisation also serves to make it almost impossible for hackers to steal information or money.
Consensus Algorithms
In the context of the Blockchain technology, a consensus algorithm, through pre-defined rules, is a means to achieve unified agreement amongst all participants of the Blockchain network and implying everyone accepts it.
It is what makes a Blockchain network fully execute its capabilities to make it secure, decentralised and achieve reliability. Also, the next block in a Blockchain is fully validated by preventing Double-Spending[1] and the economic interest of participants are aligned. Given that the technology continuing to evolve so would the Consensus Algorithms. There are multiple kinds of consensus algorithms (see Appendix I) which currently exist, each with different fundamental processes, advantages and disadvantages vis-à-vis the use cases they are used for.
The consensus algorithm is the core of a Blockchain, the part that truly gives it shared and decentralized control over the data. Blockchainplatform.io contains a list of major DLT/Blockchain platform that use a diverse range of consensus algorithms.
Tokenisation
One of the most interesting innovations Blockchain technology is the ability to create Tokens. It is merely a reference or unique identifier mapping a sensitive data element representing some information or asset. Something similar would be loyalty points or airline miles used by several enterprises for decades. Tokens may also be referred to as coins. For example, Bitcoin, Litecoin and other cryptocurrencies that function over a Blockchain. The concept of Tokens serves as an easily programmable and transferrable form of value that can represent money and other things as well. For example, Artwork, Music, Real Estate and others.
Tokens power Blockchain platforms and serve as an essential incentive layer to the functioning of the Blockchain network. For example, miners get Bitcoins as the payment for computation and network resources. Tokens are highly customizable and are different classifications of Tokens and their uses. Some of the types of Tokens are listed here
- A token can represent a Currency, in the case of cryptocurrencies like Bitcoin
- When a Token represents the value of the asset, it represents. It can be a Security Token. However, if a Token represents a share in an enterprise, it can be an Equity Token.
- Utility Tokens are sort of coins tokens (points/coupons) that can be spent within the ecosystem of the Blockchain-based system for the purchase of goods and services.
- Debt Tokens represent debts like bonds or mortgages.
Smart Contracts
Nick Szabo, an American computer scientist first proposed Smart Contracts in1994 as the phrase and concept with the goal of bringing what he called the “highly evolved” practices of contract law and practice to the design of electronic commerce protocols between strangers on the Internet (BitcoinWiki, 2019).
In the current Blockchain technology smart contract also known as a cryptocontract, is a computer program that runs on a Blockchain network such as Ethereum. With predefined the rules and penalties coded as per an agreement, Smart Contracts help in automatic exchange of money, property, shares, or anything of value in a transparent, conflict-free way with validation and enforcement (where possible) of contractual obligations while avoiding the services of a middleman. In the event of contractual breaches or aborts, the decentralized Blockchain ensures that honest parties obtain commensurate compensation. The existing technology of Smart Contracts lack transactional privacy but can hide the individual identity
According to the European Commission report, a DAO (Decentralized Autonomous Organization), still at an evolutionary stage is seen as the most sophisticated and complex form of a Blockchain smart contract (BlockchainHub, n.d.). It can be a virtual organization with its by-laws coded in the form of Smart Contracts. There is a hierarchical structure to managed by humans. Instead, people interact with each other according to specified protocol coded and enforced on the Blockchain. This concept is at a very initial stage and needs to evolve and experienced to prove that its real-world use case implementations can be viable.
Regrding DAOs, Finley, (2014) reported that Vitalik Buterin, “envisions far more complex smart contracts, including joint savings accounts, financial exchange markets, or even trust funds. Theoretically, these contracts would be more trustworthy because – if the software is properly designed – no one could cheat. Many bitcoin geeks even believe that smart contracts could lead to the creation of “autonomous corporations” – entire companies run by bots instead of humans”.
Incentivizing participation
For a Blockchain network to be effective it is important that there are plenty of incentives for the participants. For example, miners, run the nodes to validate and create blocks, store Blockchain data get rewarded through the contributions they make to a network. Experts are rewarded to uncover bugs, bring improvements and uncover security flaws through bounties or to embrace new coins through airdrops. Users are incentivised through revenue-sharing encouraging loyalty to the networks and promote participation. Therefore, combinations of diverse schemes of incentivisation are embedded into the very design of the Blockchain system to ensure participation and success.
Transfer of Value over the internet
Blockchain makes it possible to transfer value using the internet. Money needs to leave one account and recorded in another to record the transfer of value. The same dollar cannot be spent twice. It is not like a digital photo one can copy to several email addresses while keeping a copy of the same in one’s own computer. For an online transaction on internet, or transfer of funds, the double-spend problem is solved by clearing each transaction using the centralized databases of a commercial bank, credit card or money transfer companies. While some transactions are cleared in a short time, settlements for some parts of the world can take days and involves costs in terms of commissions and other expenses. Leveraging the Blockchain peer-to-peer network with cryptography, a consensus mechanism, trusting code and algorithms solves this double-spend problem within minutes to settle the transactions in a transparent and fully traceable manner.
References:
- Alexandre Grech and Anthony F. Camillieri (2017) JRC Science for Policy Report – Blockchain for Education, Luxembourg, European Union [Online]. Available at https://pt.slideshare.net/eraser/blockchain-in-education-alexander-grech-anthony-f-camilleri-editor-andreia-inamorato-dos-santos.
- BitcoinWiki (2019) Nick Szabo BitGold – Satoshi Nakamoto – BitcoinWiki [Online]. Available at https://en.bitcoinwiki.org/wiki/Nick_Szabo (Accessed 7 July 2019).
- Cavoukian, A. (2017) ‘“Global privacy and security, by design: Turning the ‘privacy vs. security’ paradigm on its head”’, Health and Technology, vol. 7, no. 4, pp. 329–333 [Online]. DOI: 10.1007/s12553-017-0207-1.
- Don Tapscott and Alex Tascott (2018) Blockchain Revolution, Updated Edition., New York, Penguin Random House LLC.
- Finley, K. (2014) ‘Out in the Open: Teenage Hacker Transforms Web Into One Giant Bitcoin Network’, Wired [Online]. Available at https://www.wired.com/2014/01/ethereum/ (Accessed 12 July 2019).
- Frankenfield, J. (2019) 51% Attack [Online]. Available at https://www.investopedia.com/terms/1/51-attack.asp (Accessed 10 July 2019).
- Goodey, A.-R. (2018) ‘Blockchain Solves The Problem Of Manipulation – Crypto Clothesline’, [Online]. Available at https://www.cryptoclothesline.com/blog-posts/blockchain-solves-the-problem-of-manipulation/ (Accessed 12 July 2019).
- Rachel Botsman (2017) Who Can You Trust?: How Technology Brought Us Together and Why It Might Drive Us Apart, Public Affairs.
- Scott, Z. (2018) Digital Feudalism [Online]. Available at https://towardsdatascience.com/digital-feudalism-b9858f7f9be5 (Accessed 12 February 2019).
- Steven T. Snyder (2019) The Privacy Questions Raised by Blockchain [Online]. Available at https://www.bradley.com/insights/publications/2019/01/the-privacy-questions-raised-by-blockchain (Accessed 15 May 2019).
- UNCTAD (n.d.) Data Protection and Privacy Legislation Worldwide [Online]. Available at https://unctad.org/en/Pages/DTL/STI_and_ICTs/ICT4D-Legislation/eCom-Data-Protection-Laws.aspx (Accessed 19 May 2019).
- Wikipedia (2019) ‘Vitalik Buterin’, Wikipedia [Online]. Available at https://en.wikipedia.org/w/index.php?title=Vitalik_Buterin&oldid=905281222 (Accessed 12 July 2019).
[1] Double-spending refers to the possibility of a digital currency being spent twice.
Also read:




Thanks for providing the in-depth knowledge for the Blockchain technology. I look forward to see many more inspiring articles by you.
https://hashstudioz.com/blockchain-development-company.html
Thank you. I am glad you found it useful.
Good Information, I have some interesting articles for you, please check it out:
https://www.blockchain-council.org/category/blockchain/
Thanks
https://www.sellbitbuy.net/paxful-clone-script
Thanks for sharing